76
Casio Calculators / Prizm BASIC libs
« on: February 14, 2011, 04:34:22 pm »
I think the question says it all.
|
This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to. 76
Casio Calculators / Prizm BASIC libs« on: February 14, 2011, 04:34:22 pm »
I think the question says it all.
77
Casio Calculators / PrizmLib« on: February 11, 2011, 01:18:53 am »
I've recently been working on a library of routines for the Prizm. I intend these to eventually form the basis of an on-calc language similar to Axe, but the routines are for the moment being written so that Assembly programmers can use them. At the moment, I am working on multiple libraries, of which the math library is the farthest along. Here are a few routines in case anyone wants to use them.
Code: [Select] /* Mod */Code: [Select] /* Arbitrary precision addition (unsigned) */Code: [Select] /* Arbitrary precision subtraction (unsigned) */Code: [Select] /* Linear Congruential Random Number Generator */Let me know if you have any routines you'd like to submit, optimizations to make or bugs to report. 78
Casio Calculators / WFRNG 4 teh Prizm« on: February 10, 2011, 10:55:52 pm »
After losing track of the epic might of WFRNG in my hard drive, I have resurrected WFRNG from the dead. This is a new era in programming: WFRNG in eight fun and wacky colors! I attempted to take a screenshot, but my camera esploded from the sheer awesomness of it. Run it at your own risk, as Prizm's have been known to become sentient as a result of it. Mine now programs itself.

79
Miscellaneous / Math functions« on: February 09, 2011, 03:26:01 pm »
If you would like to see non-math related things, like string operations, just mention them...
...Unless it involves division by 0. I don't want to create a wormhole in my Prizm. 
80
TI-BASIC / Tilemap optimization« on: February 06, 2011, 08:20:48 pm »
Can anyone make a faster tilemapping engine than this? It can display a full map in approximately a tenth of second.
 The engine has to have a rudimentary object collection system, some sort of object display screen, complete collision detection, and full screen map display... ... in pure BASIC. 81
Math and Science / Cellular automata« on: January 30, 2011, 06:36:56 pm »
Does anyone have an interesting CA that they like?
This is one of my favorite 1D CA (because of its Turing completeness) and it was generated by the first Axe program I ever made. Rule 110: 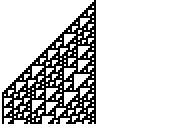
82
Casio Calculators / SH3 programming tutorials« on: January 29, 2011, 05:03:54 am »
Introduction:
To get started in SH3 programming, a background in z80 or other low level programming is helpful, but it's not necessary. Also, the information contained herein is accurate to the best of my knowledge at the time of this posting, but may not be in the future. Be sure to double check other documentation if something doesn't seem to work. Also, for future reference, the [current] standard documentation can be found at these links: SH3 Hex equates SH3 Assembly language documentation 7705 SH3 processor documentation In order to understand SH3 hex, you need to understand the basic facts about the processor itself. The SuperH 3 processor is what's known as a 32 bit RISC processor. This means that the processor likes to operate on 32 bit chunks of data. This means that each bit (which is a binary 1 or 0 in memory) is grouped with 7 other bits to form a group of 8 bits known as a "byte." Two bytes are grouped to form something called a "Word," which has 16 bits. Two words (4 bytes or 32 bits) are grouped together into a large group known as a "Longword" in SH3 Assembly. RISC stands for Reduced Instruction Set Computing and refers to the design philosophy of the processor. Instead of providing a lot of complex and slow instructions, the designers of the chip decided to go for a smaller instruction set which could be processed faster and increase the number of instructions per kilobyte of code. Unlike many other 32 bit chips which have 32 bit instructions, each SH3 command is specified by a string of 16 bits. This has the side effect of making each instruction very fast (on the order of 2-4 times faster that similar instructions on other chips at the same clock frequency). One example of this instruction reduction is that the instruction to move a byte from the location four bytes farther in the code into the R1 register would be 1110000100000100. If this seems a bit impractical to program in, it is. No one wants to type in 16 1's and 0's every time they do anything. If one did, even a small program would look like this: Quote 11011000 00000110 11011001 00000110 11011010 00000111 10011011 00010000 10011100 00010000 10011101 00001101 00101010 11000001 00101001 10110001 00101000 11010001 00000000 00001001 00000000 00001001 00000000 00001011 00000000 00001001 11111111 11111111 11111111 10000000 11111111 11111111 11111111 10000100 11111111 11111111 11111111 10000110 00000000 00001001 00000011 00000000 01011010 01111010 10100101 01100101 If you were wondering, that particular code overclocks the processor. But instead of binary, something called hexadecimal is used. As it turns out, every sequence of four bits can be specified by a single hexadecimal letter. 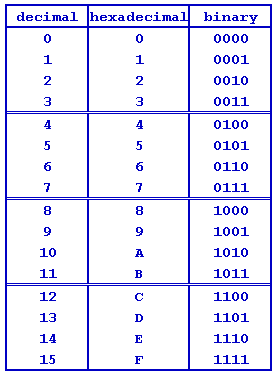 When you convert the previous binary to hex, it becomes much more manageable: Quote D806 D906 DA07 9B10 9C10 9D0D 2AC1 29B1 28D1 0009 0009 000B 0009 FFFF FF80 FFFF FF84 FFFF FF86 0009 0300 5A7A A565 Which would you rather use? In any case, hex editors, such as my personal recommendation of HxD are available and Binary editors are not. Each instruction operates based on what are known as registers. There are 16 general purpose registers in the processor, labeled R0 through R15. The first 8, R0 through R7, are switched depending on which privilege mode the processor is operating in at the moment. The last 8, R8 through R15, are the same no matter what mode the processor is in. Of these registers, only two have any uses other than to hold data, R0 and R15. R0 is automatically accessed by some instructions and R15 is used as a stack pointer during exception handling. If there are interrupts present or the processor throws code errors, then R15 will probably be corrupted. There are also two other types of registers, called system registers and control registers. These have their uses, but they can have specific methods for accessing and writing to them may cause unintended effects if not controlled. We'll deal with specific registers as we come to them, but understand that any register that is not in the range R0 through R15 should not be used for holding data. Now, to program in SH3 at the current period of time, you need to modify an existing add-in program, three of which are available here. I recommend the Conversion add-in because it is the easiest to modify. Remember to fill all of the code (except for the last four bytes) after address 7000 with repeating sequences of 00 09. If you use HxD, you can write the code in another document and copy/paste it into the add-in. After that, you must re-compute the security checksums, but that is beyond the scope of this article and will soon be rendered unnecessary. Programming: Since all of the basics are out of the way, we can begin with the programming. The first thing almost every program needs is for the program to be set to an initial state. This is known as data loading and is very easy on most processors. Unfortunately, it can be royal pain on the SH3 because of its RISC design. When you need to load a byte into a register Rn, you'd write Enii, where n is the number of the register in hex and ii is the byte of immediate data. For example, EA04 would load register R10 with 0x04h. But, wait, R10 is a 32 bit register, right? It can't hold only 8 bits. Well, that's right, but the processor does something known as sign extension where the byte is extended to 31 bits and placed in the register. The highest bit in the register, bit 32 is used to hold the sign of the number. In this case, it would be positive. If the byte were FF, then the register would hold the two's complement of the number, which is a negative number. If you want to load a larger chunk of data, the method is more complicated. For loading words, the instruction is 9ndd. For longwords, the instruction is Dndd. The dd byte refers to a displacement, which is multiplied by 2 for words and by 4 for longwords. The product is then added to the program counter and the word or longword starting at that location is placed in Rn. If the instruction is loading a word, then it will sign extend the word as with loading bytes. Here's some example code: Code: (Longword loading example) [Select] ---------------------------This will take the longword FFFF FF80 starting at address 0006 and place it in R15. This will just allow you to load a program from nearby constant locations within the program. It's also important to be able to important data from other places in the calculator. This handled by another set of instructions, 6nm0, 6nm1, and 6nm2. These instructions will move a byte, word, and longword from the address contained in Rm to Rn. Rm is called a pointer because it "points" to the data. In reality, if you were use this for its obvious use of importing sets of continuous data, it'd be less efficient that another routine, but we'll get that more efficient and obfuscated method to that later. So, let's write a program to import some data about the processor from the FRQCR register, which controls the processor clocks. Code: [Select] 0009 // This just increments the program counter without doing anything.If you couldn't tell, this program looks up the address of the FRQCR register (which is a 16 bit control register, hence the two byte imports) and then uses that address as a pointer in the other commands. Now you could use move a word into R9 and be done faster, but that's beside the point. As you can see, importing data is a pain, but it's possible. Arithmetic: Now that you can move data around, you'll at some point want to work with it. This is often done with the arithmetic commands. Even though the SH3 CPU is a RISC processor, it still has enough math commands to make it usable. Most of these are variations on standard addition, subtraction, multiplication and division. For example, let's say you were using R1 as a counter variable and you wanted it to increment during a loop. An easy, efficient way to do this would be 7101, which adds the quantity $01 to R1. However, this does not register an overflow or carry in the register. More later 83
Are you an expert at Intercal?
Do you think Malbolge is for wimps? Can you program Brainf*ck in your sleep? Do you not value your sanity? If you answered yes to any of these questions, congratulations, you are officially insane. You're also a perfect candidate for Antenora. Antenora is a language designed specifically to fix the flaws found in Malbolge that allowed the creation of the famous Hello World program by Andrew Cooke. It attempts to tread the thin line between allowing programs to theoretically be written and being impossible to use, all while making actual programs no more than a pipe dream. Here is the first language specification that I am currently implementing: Programs will be run by a very simple process. First, programs must be written in base 5i (that is the imaginary number i, not a variable) and will be converted at load time to quinary. Then, the interpreter will divide the converted source into multiple sections of 160 bits and encrypt each of them using a SHA-1 cryptographic hash. The encrypted data will then be treated as executable code and executed by the interpreter. Antenora is heavily based on Malbolge and thus has a very similar design. One aspect carried over from Malbolge are the three registers, renamed to A, B, and P. A and B are general purpose registers which can contain any data recognized by the interpreter. The third register, P, is a pointer register and points to the location of the current instruction as well as the current cell in the data array. Unlike in the normal variant of Malbolge, P also has no official limitation on size, although it will due to physical constraints for this implementation. The data array itself is an array of equal size as the program and each cell has a corresponding instruction associated with it. Any Malbolge programmer should become quickly acquainted with the instruction set, which includes ten instructions: { : sets B equal to A ] : Sets the value of the cell currently pointed to by P equal to the quinwise addition of registers A and B. ∫ : Sets P to the value of the cell pointed to by the current value of P. In other words, an absolute jump. ¿ : Sets P to the value of the cell pointed to by the value of the cell currently pointed to. A jump using indirect addressing. @ : Sets the value of A equal to the value of the current cell pointed to by P. △ : Stores the value of the next instruction in the cell currently pointed to by P and increments P by 2. ↑ : Sets the value of the instruction currently pointed to by P to the value of the cell currently pointed to by P. ► : Performs a "schizophrenic" operation. Takes the operation of the instruction pointed to by the cell currently pointed to by P, then changes the value of the cell to the location of the original instruction in another array. ⇒ : Reads the value of the current cell in the array and ouputs it into the screen at the location pointed to by the contents of A (Y) and B (x). ° : Rotates the value of the cell right Quinwise a number of times equal to the value of the cell pointed to by P+1, then jumps to the location pointed to by the value of the cell pointed to by P+1, treating the instruction P+1 as a ∫ operation. Keep in mind that all Antenora operations are done in Quinary and that any invalid instruction will immediately result in a RAM clear or otherwise crash. The only way to end a program is to reach its last instruction, which will exit provided that the instruction is not a jump instruction. Let me know if anyone thinks I should add anything or if they see any security flaws in Antenora. It is truly evil 
84
Axe / Parsing files« on: January 23, 2011, 03:56:01 pm »
How would one go about parsing a file in Axe? You'd clearly have to find the program's token in the VAT (Input?), but once you've found the pointer, how would you read the file itself? Would you simply treat it as a string and step through it or would you need to do something more difficult?
85
Miscellaneous / Hierarchy of Programming languages« on: January 23, 2011, 02:05:19 am »
What languages are the most powerful or the most useful? What are the least powerful and least useful?
Most Powerful: Hex Malbolge Assembly C++ C Python Java BASIC Casio-BASIC TI-BASIC Brainf*ck Whitespace TI-Nspire BASIC Most useful (general purpose): C++ C Python Assembly Hex Java BASIC Casio-BASIC TI-BASIC Brainf*ck Whitespace TI-Nspire BASIC Malbolge 86
Casio Calculators / How to fix your Prizm« on: January 20, 2011, 01:10:19 pm »
Since I have screwed up my Prizm multiple times already, I figured it might be best to start putting together a guide for how to fix your Prizm:
If you send an invalid data file to the Prizm, such as a BASIC program with incorrect security bytes, the Prizm will return a Data Conversion error when it attempts to write the data back to memory. The calculator will also relocate all offending programs to another folder labeled Safe-F, which will not show up in the memory manager on-calc. As far as I have been able to tell, the only way to remove files from this folder is to do it manually through USB. The calculator may also delete the Programs folder if all of the programs are invalid. To fix this, simply create a new folder named "PROGRAMS" in the @MainMem directory and delete the Save-F folder. Occasionally you might get a memory Full error even though you have >9000 bytes of memory left. The only way to fix this is either to remove the program that is causing the memory error or to reset your main memory. 87
TI-BASIC / Cage match battle engine« on: January 18, 2011, 12:23:44 pm »
I need Ideas to improve the quality of my battle engine. I need attacks for both monsters and the hero.
Thanks in advance. 88
Casio Calculators / Help with SH3 disassembler« on: January 14, 2011, 03:22:32 pm »
As some of you may have noticed, we've been busy hacking the Casio-Prizm and have had some success. However, since we finally have the hex equates for all SuperH 3 Assembly commands, a disassembler is required to properly analyze the Prizm. While other disassemblers have been written, only one in a very expensive commercial package is available for newer OSes. The others, insofar as I have been able to find, are all incompatible and even worse, use the Assembly language of a slightly different processor. So, if you have any computer programming skills, I'd appreciate help with this. Just send me a PM if you're interested.
Thanks, Qwerty. 89
Casio Calculators / Unknown code« on: January 09, 2011, 04:38:57 pm »
This topic will be for the discussion of Prizm code that seems odd or puzzling.
For example, the code between $01FE and $10D8 is odd. It follows a very specific pattern: Code: [Select] 03 00 04 00 05 00 06 00 07 00 08 00 09 00 0A 00 0BI can't figure out what this would be. It repeats until every other byte is 07 and ends with a sequence of FF's and 00's 90
TI Z80 / Command line« on: January 05, 2011, 11:07:51 pm »
This is an evolution of an old project of mine called TI-explorer. It's exactly what the name suggests: a calculator command line.

|
|
|